Medicine Group. 2023 December 31;4(12):1738-1744. doi: 10.37871/jbres1859.
Machine Learning Model for Chronic Disease Prediction
Raza Nowrozy*
- Electronic health records
- Chronic
- Machine learning
Abstract
Chronic diseases are a class of illnesses with complex etiologies, long-lasting or persistent symptoms, and are frequently referred to as chronic non communicable diseases. The most significant public health issues in the world are the leading chronic diseases, which include heart disease, cancer, chronic obstructive pulmonary disease, stroke, and diabetes. Both developed and developing nations experience significant health and financial costs as a result of these diseases. Some risk behaviours, such as tobacco use, poor nutrition, and excessive alcohol consumption, are the root cause of many chronic diseases. The various schemes are designed for the chronic disease prediction. The machine learning models for the chronic disease prediction is analysed in terms of certain parameters.
Introduction
The rise in chronic illnesses has led to a more health-conscious society, where patients are now seen as "health consumers" actively seeking improved health management. Detecting diseases at an early stage necessitates a healthcare system capable of continuously monitoring health status [1]. Timely identification of physical and mental changes requires frequent and sensitive measurements of physiological and behavioural data. Physiological monitoring entails tracking variations in metrics like heart rate, blood pressure, blood glucose levels, and weight. However, gathering behavioural data demands continuous monitoring, a challenge often hindered by the clinical setting's limitations. The ubiquitous healthcare (u-Health) framework emerges as a solution, revolutionizing medical history by offering real-time insights into diseases and alerting patients to potential chronic issues [2]. Additionally, u-Health enables healthcare providers to remotely monitor patients' physiological data in real-time.
The healthcare sector generates vast volumes of data from diverse sources, including relational databases, XML, ADL files, images, scans, and tabular records, among others. These data possess varying structures and meanings, often exhibiting vagueness and imprecision. The realization of u-Health goals hinges on the harmonization of this data through standardized methodologies. The Electronic Health Record (EHR), a prominent eHealth application, holds the potential to transform the healthcare industry from paper-based practices to a digitalized realm [3]. Its core objective lies in maintaining a documented care record that aids current and future treatments by the same or different medical professionals. The integration of modern technology in healthcare has led to a proliferation of medical data from diverse sources such as monitoring, diagnosis, clinical notes, and billing services. EHR plays a pivotal role in amalgamating these varied patient data from heterogeneous systems, a fundamental prerequisite for effective knowledge discovery [4].
The increasing adoption of Electronic Health Records (EHRs) has raised significant concerns regarding privacy and security. Despite implementing various measures, patient privacy remains vulnerable due to unreliable data-sharing methods and inadequate privacy policies. Notable data breaches in systems like Australia's My Health Record and the UK's National Health Service have resulted in substantial financial losses [5]. Furthermore, the growing utilization of Machine Learning (ML) in healthcare for diagnostics and drug discovery intensifies these concerns. ML models often require extensive patient data, including sensitive genetic and clinical information, raising ethical and legal considerations. The widespread application of ML in healthcare emphasizes the importance of addressing the ethical, legal, and privacy challenges posed by Artificially Intelligent Systems (AIS) like ML, deep learning, and Natural Language Processing (NLP) algorithms. Context-sensitive privacy policies are crucial for tailoring privacy settings and access controls based on data sensitivity, ensuring adequate protection for sensitive health information [6].
Several privacy policies, including the Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), and various other regulations and principles, have been enacted to address privacy concerns on both local and global scales. Nevertheless, despite these established local and international privacy frameworks, instances of privacy breaches within existing Electronic Health Record (EHR) systems have eroded trust in health-related IT systems [7]. This erosion of trust has led numerous users to opt out of systems like Australia's My Health Record (MHR) platform. These conventional privacy standards often lack specificity, underscoring the necessity for an innovative privacy model that offers enhanced protection for patients' privacy within EHR environments.
Contemporary approaches to secure Electronic Health Records (EHRs) revolve around systems that emphasize confidentiality, authentication, integrity, trust, verification, and authorization. Intrusion Detection Systems (IDS) have been proposed to identify and classify suspicious activities and security breaches [8]. However, these systems could still be susceptible due to outdated databases and potential tampering of patient data through malware or unauthorized access. To counter these vulnerabilities, privacy-preserving Machine Learning (ML) frameworks have emerged, leveraging techniques like homomorphic encryption, secure multiparty computation, and differential privacy. These methods shield sensitive patient data while upholding analytical accuracy. Notwithstanding these advancements, the quest for more robust and holistic solutions to safeguard healthcare information persists [9]. Further research is imperative to bridge this gap, focusing on a secure and privacy-centric health data sharing framework within the EHR realm. This framework should encompass all pertinent stakeholders, ensuring the privacy of patients' information.
The healthcare domain presents a distributed, dynamic, and heterogeneous nature, with vast daily data updates, necessitating a hierarchical structure with an expansion design for effective system operation. Ontologies hold a crucial role in establishing distributed and interoperable Electronic Health Record (EHR) environments [10], offering consistent semantics and explicit formal models. Semantic Web (SW) technologies facilitate data reuse and sharing across enterprises, applications, and communities, thereby achieving Semantic Interoperability (SI) within EHR systems. At the core of SW, ontologies serve as data models that represent a specific domain's concepts and their relationships in a formal semantic manner using axioms [11]. This enables both human and machine comprehension of exchanged data's meaning. In recent years, ontologies have found utility in diverse fields, including software engineering, artificial intelligence, natural language processing, and biomedical informatics. Their application extends to human communication enhancement, software system interoperability, and software quality and design improvement. A key advantage of ontologies lies in their ability to establish consensus among various parties, making them closer to becoming a standardized data model than other alternatives [12].
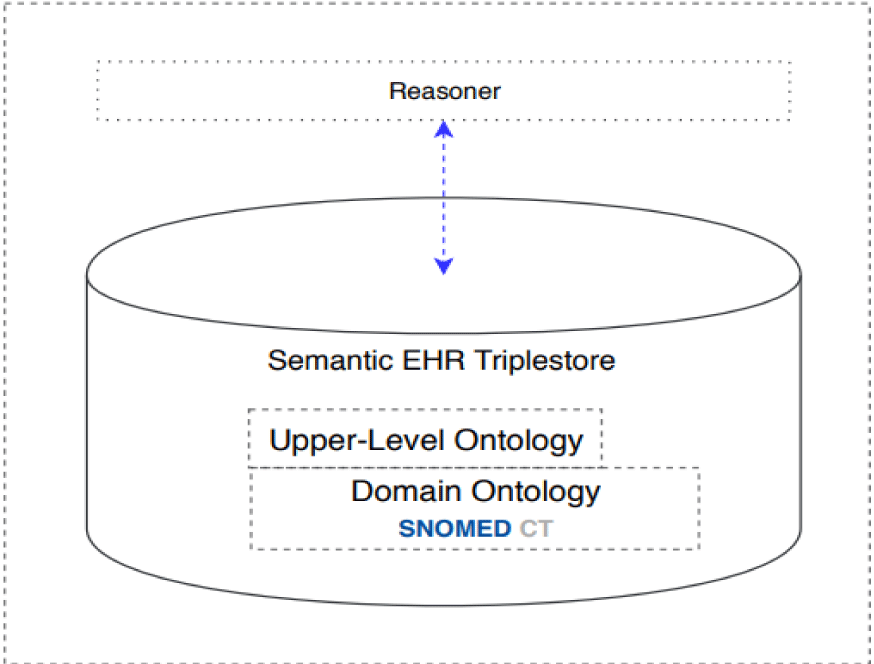
Figure 1 illustrates the knowledge structure of an EHR triplestore, wherein semantic middleware leverages ontology to facilitate semantic integration and functional collaborations between IoT healthcare information systems and EHR systems. In this process, a dedicated semantic triplestore is crafted for efficient management and storage of EHR data. The ontology domain is effectively modelled using the Web Ontology Language (OWL), ensuring a formal knowledge representation within the store [13]. Specifically, our approach adopts the OWL version of SNOMED-CT, chosen for its growing significance as an extensive global terminology encompassing diverse clinical information found in EHRs, further enriched by mappings to various classification systems. The model encompasses both an upper-level ontology, representing abstract and overarching concepts shared across domains, and a domain ontology, housing SNOMED CT content, tailored to more specific concepts. The stored semantic EHR data is queried and reasoned using the SPARQL language [14].
The utilization of ontology-based approaches is proving to be a valuable asset in enhancing the security of Electronic Health Records (EHRs). These innovative methods leverage ontology, which structures knowledge into well-defined categories and relationships, to significantly bolster the security framework of EHRs [15]. One crucial role of ontology-based security is its ability to establish a robust and standardized foundation for data classification and access control within EHR systems. Through the categorization of medical data into distinct classes and hierarchies, these approaches ensure that specific information can only be accessed by authorized personnel. This organized structure reduces the risk of unauthorized breaches and reinforces overall data governance [16]. Additionally, ontology-based security solutions provide the advantage of dynamic access control mechanisms. These mechanisms can adapt to changing contexts and user roles, enabling real-time adjustments to data access privileges. For instance, a healthcare professional conducting patient diagnoses may require varying levels of data access compared to administrative staff overseeing billing information.
Literature Review
Nowrozy R, et al. [17] suggested an innovative Machine Learning (ML), based privacy framework for Electronic Health Records (EHR) systems in which a conceptual privacy ontology and ML techniques were deployed. This framework was employed for dealing with the issues occurred in HER systems such as to balance the privacy and availability, accessibility, and authentic compliance. Thus, a universal privacy framework was generated for managing and sharing personal and sensitive data of patients across diverse platforms, namely MHR and NHS systems. Furthermore, a several Bidirectional Encoder Representation from Transformer (BERT) methods were implemented for distinguishing amid genuine and dishonest privacy policies. The results indicated the supremacy of the Distil BERT and effectiveness of the suggested framework for recognizing redundant privacy policies and classifying them as authentic and malicious.
Alsubaei F, et al. [18] introduced a recommendation tool for modeling Internet of Medical Things (IoMT) notions and security concerns and suggested security measures later on. In this approach, a semantically enriched ontology was adopted for modelling the elements of IoMT, safety issues, and measures. Moreover, the context-aware rules were comprised in this ontology for providing reasoning so that a recommendation system was developed for supporting users in making well-educated decisions. The introduced tool was exploited for classifying security threats occurred before the IoMT stakeholders and security controls in an automatic way for tackling every threat. Diverse security assaults were considered for computing the introduced tool with regard to efficacy and totality. According to experiments, the introduced tool was effective for providing essential security solutions.
Rahmouni HB, et al. [19] discussed that for protecting the patient data when the required medical processes were provided, various computerized methods were required in Health Information System (HIS). Thus, a robust mechanism was developed for modelling the medical pathway specifications to execute data driven medical procedures. For this, the sensitive data was differentiated from other data and the notions for protecting the personal data and the Protected Health Information (PHI) were recognized. Every clinical task was executed in an effective way in which data was processed and transmitted. The privacy tags were employed for providing the level of protecting data and the HL7 standard for predating the data component after assigning labels to them. This tagging technique was useful to map the extracted data, having diverse categories, onto a set of privacy necessities of the HIPAA legislation. Hence, the developed mechanism protected the data and privacy seamlessly and with transparency. The HL7 was effective to explore and parse the data that led to describe measures for protecting the clinical data.
Costa LD, et al. [20] designed a blockchain-based protocol called Sec-Health for securing the health records when the security issues were tackled. This protocol was exploited to tackle issues related to keeping the data confidential and reliable, controlling the access, access revocation, emergency access, etc. The analysis exhibited the robustness of the designed protocol over the traditional methods. Unlike the method planned on the basis of trusted or semi trusted server, this protocol offered various decentralized attributes which prevented one single entity from negotiating the healthcare system. In addition, this protocol had potential to deal with the issue related to satisfy all major properties of health records. The results exhibited that the designed protocol was robust against various assaults and helped in mitigating the time for accessing the health records around 90% and memory overhead up to 50% in comparison with other methods.
Zhuang Y, et al. [21] presented a patient-centric Health Information Exchange (HIE) approach with the help of unique features of blockchain which was unhackable. A smart contract feature, a programmable self-executing protocol on a blockchain, was considered for formulating a blockchain framework. This framework was utilized for protecting the data security and privacy of patients, ensuring data provenance, and providing control to the patients for their health records. The data was segmented and an “allowed list” was provided to clinicians for accessing their data and attained a patient-centric HIE. Two layers of security settings were adopted for ensuring that only authorized users were capable of executing certain smart contract functions and mitigating the data breaching. The data was kept reliable using a hashing mechanism. The touchpoint selection was generated for clinicians for selecting the health records regarding the patient visit for which entire records were not considered. The experimental results confirmed that the formulated approach was feasible, stable, secure and robust for protecting the health records.
Ahamad SS, et al. [22] projected a Secure and Resilient Scheme for Telecare Medical Information Systems (SRSTMIS) for validating the privacy and security of patient’s credentials and Mobile Healthcare Applications (MHA) and a secure protocol was put forward. A White-Box Cryptography (WBC) was employed for securing the keys in the healthcare applications. The projected approach was utilized to model the threat and Microsoft Threat Modeling tool 2016 was executed for quantifying this approach. The results on Burrows, Abadi, and Needham (BAN) logic and Scyther tool exhibited the robustness of this approach against Denial of Service (DoS), multi-protocol, Blue Borne, Distributed Denial of Service (DDoS), reverse engineering, insider, outsider and Phlashing assaults. Moreover, this approach was capable of tackling information leakage from sensors while transmitting the data from healthcare applications of the sensors and smart phone and ensuring HIPAA regulations. On Android Studio, the projected approach was secure, resistible and consumed few resources.
Bae YS, et al. [23] presented a block chain-based mobile platform known as Health Pocket for transmitting reliable health information with proven integrity. For this, a dynamic consent system was implemented on the basis of HL7 FHIR standards. This model allowed the subjects to provide their consent for sharing specific medical and PGHD with proper approval, and to transform every response into the JSON format with FHIR compatibility. A testing was performed on this model for depicting the Health Information Exchange (HIE) amid primary and tertiary medical institutions. This model was adopted by116 subjects for sharing the health information for at least one month. Besides, this model assisted the medical staff in accessing the medical information transmitted via the participants and starting the treatment. The results depicted that the presented model offered higher mean overall satisfaction of 4.67 points with the Health Information Exchange Service (HIES). Moreover, this model was useful for securing and protecting the health information, and alternating the data blocks became impossible.
Hamdi H, et al. [24] suggested a new Formal Concept Analysis (FCA)-based heuristic algorithm for preserving the security and privacy of sensitive e-Health information on the basis of itemset hiding methods. This method was known as FACHS (FCA Hiding Sensitive-itemsets) in which the constraints were deployed for alleviating the side effects and asymmetry amid the original database and the clean database by least distorting the database. The process of frequently extracting itemset was not required in this algorithm prior to masking procedure. Several reference datasets were employed for quantifying the suggested algorithm. Based on experimental outcomes, the suggested algorithm was effective concerning time efficacy to extract itemset and enhanced the security and privacy of health data.
Pinto RP, et al. [25] presented a new method based on blockchain technology in m-health systems. This method was employed to be integrated with other health systems or applications quickly and allowed a patient-user for accessing their Electronic Health Record (EHR) securely. The traceability of the data was proved in the entire and the necessary anonymity was maintained. A prototype for a blockchain-based method was designed based on Hyperledger Fabric. This method was assisted in organizing the formation of a chronologically organized and immutable health data record. An anonymous storage system was built using two separate database elements for maintaining the data traceability. For this, the sets of IDs were deployed whose storage was done in the bloc kchain. The performance and network configurations of the Hyper ledger Fabric were considered to conduct the experiments. The results revealed the feasibility of the designed method to trace the Electronic Health Data (EHR). Moreover, this method led to enhance the privacy successfully.
Lee D, et al. [26] introduced MEX change which was a novel block chain-based privacy-preserving HIE for preventing the privacy issue when the sender and concealing receiver addresses were obscured. The Smart Contracts (SCs) and workflow were presented in which ring signature and stealth address was utilized for block chain-based HIE. The software elements and process to implement the introduced approach on the Ethereum private network were explained. The transaction latency and throughput were considered to compute the introduced approach. Furthermore, the threat modeling was done on the basis of STRIDE. The results demonstrated that the introduced approach was effective to lessen the problems regarding privacy and security. Furthermore, this approach kept the data secure, reliable, transparent, available and confidential and prevented from the inference problem (Table 1).
| Table 1: Comparison table. | ||||
| Author | Year | Technique Used | Results | Limitations |
| Nowrozy R, et al. [17] | 2023 | An innovative Machine Learning (ML)-based privacy framework | The results indicated the supremacy of the Distil BERT and effectiveness of the suggested framework for recognizing redundant privacy policies and classifying them as authentic and malicious. | This framework was not suitable to be tested in real-time and on existing platforms. |
| Alsubaei F, et al. [18] | 2019 | A recommendation tool | According to experiments, the introduced tool was effective for providing essential security solutions. | The information obtained from this tool was found complicated. |
| Rahmouni HB, et al. [19] | 2019 | A robust mechanism | The developed mechanism protected the data and privacy seamlessly and with transparency. The HL7 was effective to explore and parse the data that led to describe measures for protecting the clinical data. | This mechanism was not able to tackle the human aspects for managing the privacy when the secure health data was processed. |
| Costa LD, et al. [20] | 2023 | A blockchain-based protocol called Sec-Health | The results exhibited that the designed protocol was robust against various assaults and helped in mitigating the time for accessing the health records around 90% and memory overhead up to 50% in comparison with other methods. | This protocol was ineffective for detecting and eliminating all kinds of malevolent nodes from the blockchain. |
| Zhuang Y, et al. [21] | 2020 | A blockchain framework | The experimental results confirmed that the formulated approach was feasible, stable, secure and robust for protecting the health records. | The major disadvantage was to establish a setup at every healthcare facility. Moreover, this approach was relied on properties of nodes of blockchain. |
| Ahamad SS, et al. [22] | 2022 | Secure and Resilient Scheme for Telecare Medical Information Systems (SRSTMIS) | The results exhibited the robustness of this approach against Denial of Service (DoS), multi-protocol, Blue Borne, Distributed Denial of Service (DDoS), reverse engineering, insider, outsider and Phlashing assaults and it was secure, resistible and consumed few resources. | This approach was not scalable for all kinds of security issues related to healthcare sector. |
| Bae YS, et al. [23] | 2022 | A blockchain-based mobile platform known as HealthPocket | The results depicted that the presented model offered higher mean overall satisfaction of 4.67 points. Moreover, this model was useful for securing and protecting the health information, and alternating the data blocks became impossible. | This model was depending upon independent web applications which was major limitation. Moreover, this model was not applicable for diverse medical institutions. |
| Hamdi H, et al. [24] | 2023 | FACHS | Based on experimental outcomes, the suggested algorithm was effective concerning time efficacy to extract itemset and enhanced the security and privacy of health data. | The main disadvantage was of higher response time due to huge stream applications and health databases of real time. |
| Pinto RP, et al. [25] | 2022 | A prototype for a blockchain-based solution | The results revealed the feasibility of the designed method to trace the electronic health data (EHR). Moreover, this method led to enhance the privacy successfully. | The quality of services (QoS) were mitigated in case the amount of entities such as administrations, peers, and users, were maximized. |
| Lee D, et al. [26] | 2021 | MEXchange | The introduced approach kept the data secure, reliable, transparent, available and confidential and prevented from the inference problem. | The time for processing the access requests was longer due to requirement of several elliptic curve operations while verifying the ring signature. |
Conclusion
A comprehensive security ontology model is essential for safeguarding patient data within Health Information Systems (HIS). While existing studies have focused on this, they encounter challenges including scalability, user acceptance, limited data access, inadequate security standards, evolving threats, and HIS complexity. This research introduces a standardized approach to address these issues, ensuring adaptability to dynamic threats and maintaining patient data security. The proposed model incorporates confidentiality, integrity, availability, and scalability, along with role-based access control aligned with contemporary security standards. Tested on a HIS database, the model effectively enhances security and scalability, guaranteeing safe and user-friendly patient data management. Future research could explore integrating emerging technologies like block chain, AI, and machine learning to enhance the model's effectiveness in evolving HIS environments. The proposed model provides a practical solution to HIS security complexities, warranting further investigation and application within the research community.
References
- Abounassar EM, El-Kafrawy P, ElLatif AA. Security and interoperability issues with internet of things (IoT) in healthcare industry: A survey, in Security and Privacy Preserving for IoT and 5G Networks. Techniques, Challenges, and New Directions. 2022;159-189. doi: 10.1007/978.
- Adel E, El-Sappagh S, Barakat S, Elmogy M. Ontology-based electronic health record semantic interoperability: A survey, in u-healthcare monitoring systems. 2019;315-352. doi: 10.1016/B978-0-12-815370-3.00013.
- Ahmadi M, Sheikhtaheri A, Tahmasbi F, Eslami Jahromi M, Rangraz Jeddi F. A competency framework for Ph.D. programs in health information management. Int J Med Inform. 2022 Dec;168:104906. doi: 10.1016/j.ijmedinf.2022.104906. Epub 2022 Oct 30. PMID: 36332521.
- Alvarez-Rodríguez J, Mendieta R, Cibrián E, Llorens J. Towards a method to quantitatively measure tool chain interoperability in the engineering lifecycle: A case study of digital hardware design. Computer Standards & Interfaces. 2023;86(3). doi: 10.1016/j.csi.2023.103744.
- Amato F, Casola V, Cozzolino G, Benedictis AD, Mazzocca N, Moscato F. A security and privacy validation methodology for e-health systems. ACM Transactions on Multimedia Computing. 2021;17(2):1-22. doi: 10.1145/3412373.
- Arogundade OT, Abayomi-Alli A, Misra S. An ontology-based security risk management model for information systems. Arabian Journal for Science and Engineering. 2020;45:6183-6198. doi: 10.1016/j.cose.2019.101656.
- Awotunde J, Folorunshoet O , Olawale Mustapha I, Olufunmilayo Olusanya O, Bola Akanbi M, Moses Abiodun K . An enhanced internet of things enabled type-2 fuzzy logic for healthcare system applications, in recent trends on type-2 fuzzy logic systems: Theory, methodology and applications. Springer. 2023;133-151. doi: 10.1007/978-3-031-26332-3_9.
- Bai T, Huang L, Guo S , Liu Y , Wu M , Gu G , Luo. Integrating knowledge from case report: A medical-ontology based multimodal information system with structured summary. Research Square. 2022. doi: 10.21203/rs.3.rs-2035613/v1.
- Barangi H, Rahimi SK, Zamani B, Hossein M. An ontology-based approach to facilitate semantic interoperability of context-aware systems. In International Computer Conference. 2023. doi: 10.1109/csicc58665.2023.10105364.
- Bashir A, Renuka N, Deepti M, Manju B. Interoperability of electronic health records for dyslipidemia using knowledge graphs, in 2023 13th International Conference on Cloud Computing. Data Science & Engineering (Confluence). 2023;124-129. doi: 10.1109/confluence56041.2023.10048874.
- Blanco JM, Rossi B, Pitner T. A comparative study of energy domain ontologies, in web information systems and technologies: 16th International Conference. Springer. 2020;43-58. doi: 10.1007/978-3-642-01671-4_28.
- Bughio KS, Sikos LF. Knowledge organization systems to support cyber-resilience in medical smart home environments, in cybersecurity for smart cities. Springer. 2023;61-69. doi: 10.1016/j.procs.2023.10.342.
- Cerqueira J. An ontology for context-aware middleware for dependable medical systems. In Proceedings of the 11th Latin-American Symposium on Dependable Computing. 2022;79-83. doi: 10.1145/3569902.3569947.
- Chen WT, Bria TA. A review of ontology-based safety management in construction. Sustainability. 2023;15(1):413. doi: 10.3390/su15010413.
- Michael D, Biswanath D. From ontology to knowledge graph with agile methods: The case of COVID-19 CODO knowledge graph. International Journal of Web Information Systems. 2022;5(6): 432-452. doi: 10.1108/ijwis-03-2022-0047.
- Dhillon P, Singh M. An extended ontology model for trust evaluation using advanced hybrid ontology. Journal of Information Science. 2023. doi: 10.1177/01655515221128424.
- Nowrozy R, Ahmed K, Wang H, Mcintosh T. Towards a universal privacy model for electronic health record systems: An ontology and machine learning approach. Informatics. 2023;10:(60):127-135. doi: 10.3390/informatics10030060.
- Alsubaei F, Abuhussein A, Shiva S. Ontology-based security recommendation for the internet of medical things. In IEEE Access. 2019;7:48948-48960. doi: 10.1109/ACCESS.2019.2910087.
- Rahmouni HB, Essefi I, Ladeb MF. Enhanced privacy governance in health information systems through business process modelling and hl7. Procedia Computer Science. 2019;164:706-713. doi: 10.1016/j.procs.2019.12.239.
- Costa LD, Pinheiro B, Cordeiro W, Araújo R, Abelém A. Sec-health: A blockchain-based protocol for securing health records. In IEEE Access. 2023;11:16605-16620. doi: 10.1109/ACCESS.2023.3245046.
- Zhuang Y, Sheets LR, Chen YW, Shae ZY, Tsai JJP, Shyu CR. A patient-centric health information exchange framework using blockchain technology, in IEEE. Journal of Biomedical and Health Informatics. 2020;24:(8):2169-2176. doi: 10.1109/JBHI.2020.2993072.
- Ahamad SS, Al-Shehri M, Keshta I. A secure and resilient scheme for telecare medical information systems with threat modeling and formal verification, in IEEE Access. 2022;10:120227-120244. doi: 10.1109/ACCESS.2022.3217230.
- Bae YS, Yujin P, Seung M L, Seo HH, Hyeonji L, Taehoon KO, Eunsol L, Min Park S, HyungJin Y. Development of blockchain-based health information exchange platform using HL7 FHIR standards: usability test, in IEEE Access. 2022;10:79264-79271. doi: 10.1109/ACCESS.2022.3194159.
- Hamdi H, Brahmi Z, Alaerjan AS, Mhamdi L. Enhancing security and privacy preservation of sensitive information in e-health datasets using FCA approach, in IEEE Access. 2023;11:62591-62604. doi: 10.1109/access.2023.3285407.
- Pinto RP, Silva BMC, Inácio PRM. A system for the promotion of traceability and ownership of health data using blockchain, in IEEE Access. 2022;10:92760-92773. doi: 10.1109/ACCESS.2022.3203193.
- Lee D, Song M. MEX change: A privacy-preserving block chain-based framework for health information exchange using ring signature and stealth address, in IEEE Access. 2021;9:158122-158139. doi: 10.1109/access.2021.3130552.
Content Alerts
SignUp to our
Content alerts.
 This work is licensed under a Creative Commons Attribution 4.0 International License.
This work is licensed under a Creative Commons Attribution 4.0 International License.